Kerberos
According to myth, Kerberos (you might know him as Cerberus) guards the Gates to the Underworld.MIT developed the first instances of Kerberos in the late ’80s. The protocol was named after Cerberus, a creature from Greek mythology. Cerberus was a ferocious three-headed dog who guarded Hades.
Kerberos is an authentication protocol for client/server applications. This protocol relies on a combination of private key encryption and access tickets to safely verify user identities.

Why we choose Kerbros authntication
- Plain text passwords are never sent across an insecure network.
- Every login has three stages of authentication.
- Encryption protects all access keys and tickets.
- Authentication is mutual, so both users and providers are safe from scams.

Three Main component
- client,
- server,
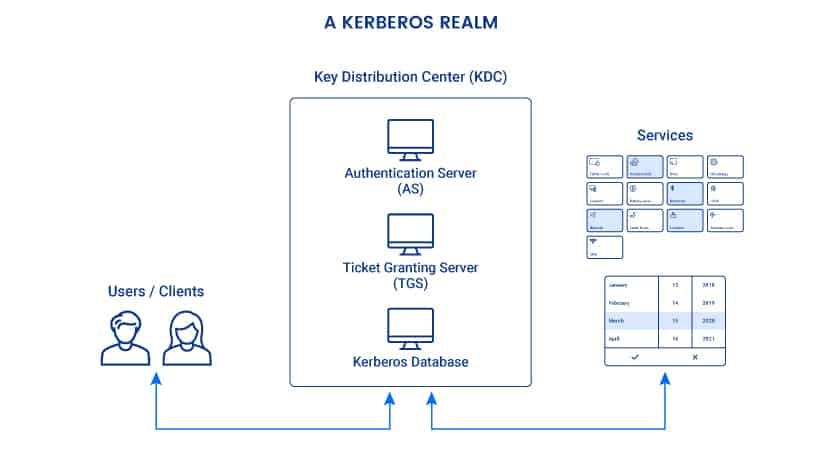
- Key Distribution Center (KDC) :- In a Kerberos environment, the authentication server logically separated into three parts: A database (db), the Authentication Server (AS), and the Ticket Granting Server (TGS). These three parts, in turn, exist in a single server called the Key Distribution Center
- An authentication server (AS): The AS performs initial authentication when a user wants to access a service.
- A ticket granting server (TGS): This server connects a user with the service server (SS).
- A Kerberos database: This database stores IDs and passwords of verified users.
Here are the most basic steps taken to authenticate in a Kerberized environment.
- Client requests an authentication ticket (TGT) from the Key Distribution Center (KDC)
- The KDC verifies the credentials and sends back an encrypted TGT and session key
- The TGT is encrypted using the Ticket Granting Service (TGS) secret key
- The client stores the TGT and when it expires the local session manager will request another TGT (this process is transparent to the user)
If the Client is requesting access to a service or other resource on the network, this is the process:
- The client sends the current TGT to the TGS with the Service Principal Name (SPN) of the resource the client wants to access
- The KDC verifies the TGT of the user and that the user has access to the service TGS sends a valid session key for the service to the client
- Client forwards the session key to the service to prove the user has access, and the service grants access.
Can Kerberos Be Hacked?
Yes. Because it is one of the most widely used authentication protocols, hackers have developed several ways to crack into Kerberos. Most of these hacks take advantage of a vulnerability, weak passwords, or malware – sometimes a combination of all three. Some of the more successful methods of hacking Kerberos include:
- Pass-the-ticket: the process of forging a session key and presenting that forgery to the resource as credentials
- Golden Ticket: A ticket that grants a user domain admin access
- Silver Ticket: A forged ticket that grants access to a service
- Credential stuffing/ Brute force: automated continued attempts to guess a password
- Encryption downgrade with Skeleton Key Malware: A malware that can bypass Kerberos, but the attack must have Admin access
- DCShadow attack: a new attack where attackers gain enough access inside a network to set up their own DC to use in further infiltration

